Gator Watch revisited
Gator Watch had a complete lack of security which made it possible to track kids all over the world and listen to private voice messages. This is supposedly fixed, at least in Norway. But is it really?
| Published: | Fri, March 30, 2018 at 07:30 |
| Updated: | Thu, April 5, 2018 at 14:30 |
| Category: |
Security
|
| Tags: |
#WatchOut
Follow-up
|
tl;dr 🔗
Gator Watch had the worst security I've seen in an online service in a long time. Now, at least the company selling Gator Watch in Norway, has released new watch firmware and new mobile apps to tackle all the issues. And what they have done is actually really impressive.
Background 🔗
Early August 2017 I found out that the Gator watches could be tracked, locations could be spoofed, and private voice messages was openly available on the Internet.
Shortly after, the Norwegian Consumer Council (NCC) also did a check on Gator Watch and a few other brands and found the same issues + illegal or non-existent terms and conditions.
The whole so-called
#WatchOut campaign led to a hectic and probably stressful few months for the companies Gator Norge, GPS for barn, Tinitell and PepCall (Xplora). The Norwegian Data Protection Authority (Datatilsynet) even forced Gator, PepCall and GPS for barn to stop all processing of personal information (Norwegian link) until they had fixed issues regarding their information security.
The Norwegian company sellling Gator Watch - Gator Norge - has since released new watch firmware and created completely new client apps. I wanted to know if the security was in order before using the watch for my own family.
Approach (technical stuff) 🔗
New firmware 🔗
The old firmware for the Gator Watch was pretty bad. The communication between the watch and the server was in clear text with out any encryption at any level. Also, there was no authentication or verification of the user. There was no session identifier, only the always fixed IMEI number. You can't really make it much worse than that.

Using the old firmware I could just change the server the watch used to learn how the watch communicated. Then I could use that knowledge to try the communication with the server pretending to be a watch. With the new firmware I don't know how to do that. Also, reading or reverse engineer the firmware is out of my expertise. This means I haven't been able to look at the communication between the server and watch. I have to trust Gator Norge when they say it now is encrypted. I also hope that it isn't possible to easily spoof other watches. Hopefully someone will take the time to analyze the new firmware that can be downloaded from Gator Norge.
New apps 🔗
The old apps and server APIs for the Gator Watch was some of the worst product I've seen in a long while - security wise.
Gator Norge trashed the old apps and server and replaced it with brand new software. I did an analysis of the Android app and also took a look at the server.
What is interesting is that this new Gator watch app - called TeleGAPP - isn't a new concept from Gator Norge. They actually released this app in September 2017, but as a app-to-app-only way of tracking friends and family. I took a brief look at the security later that fall, and I found multiple security holes. However, I never got around finishing my work or even reporting them. Shortly after I learnt that this app would soon become the new Gator watch app. So I postponed the rest of the testing - and reporting - awaiting this new version of the app. In retrospect I see that I should have reported my findings - even though it was unfinished work - I had back then because of the delays of the new app. I will probably write another post on that matter as it does have some interesting points. They have now seem to have taken down the server used back then.
TeleGAPP - utilizes a custom-made certificate pinning. This meant that I couldn't just use a regular HTTP proxy out of the box. While I see the upside of having such pinning it sure makes it much harder to simply check if an app or service is secure. The chances that a good guy will skip testing is very high, while a bad guy would go ahead anyways. In total this typically leads makes Internet less secure.
I recently posted a guide on how to crack Android apps which explains exactly what is needed for cases like this. A simple smali one-liner like return-void was all that was needed to get around the pinning.
After rebuilding the app I could use the HTTP proxy Charles to see what the encryption, authentication and data looked like. And I have to say; this new app is a whole different ball game. This app has exactly the security measures I would've expected to find in the first place.
I could try to go through all security features and what makes the app less vulnerable, but I suppose I wouldn't be able to make a complete list. All HTTP calls are of course encrypted. The authentication ends up with a bearer authorization token. The token is short lived (though even as short lived as it makes the app a bit buggy with HTTP calls failing and without proper automatic re-authentication (which in ends up as a bad user experience with error messages popping up too often (though I actually think they now have fixed in a later version))). The authorization seems to be in order. I wasn't able to access to resources or data that I wasn't supposed to have. In general the API seemed clean, secure and made by people that know what they are doing.
What I did not test, was making PUT that I should not be authorized to do. Too often I see that developers properly secure getting data, but not checking if others are allowed to update it. I typically do this if it's real quick and easy to create another user for me to test on or if I know someone else with an account that I'm allowed to test with. So I'll just assume that they have that in order as well. At least they have a good base here.
The user experience 🔗

One of the features that isn't in the new app is the mode where you could listen in on the watch without anyone knowing it. This made the old watch in to a listenting device. I really doubt that we will see that feature coming back.
Another one of the features not available is the one to - from parent to kid or the other way around - leave a voice message if you are unable to get hold of the other.
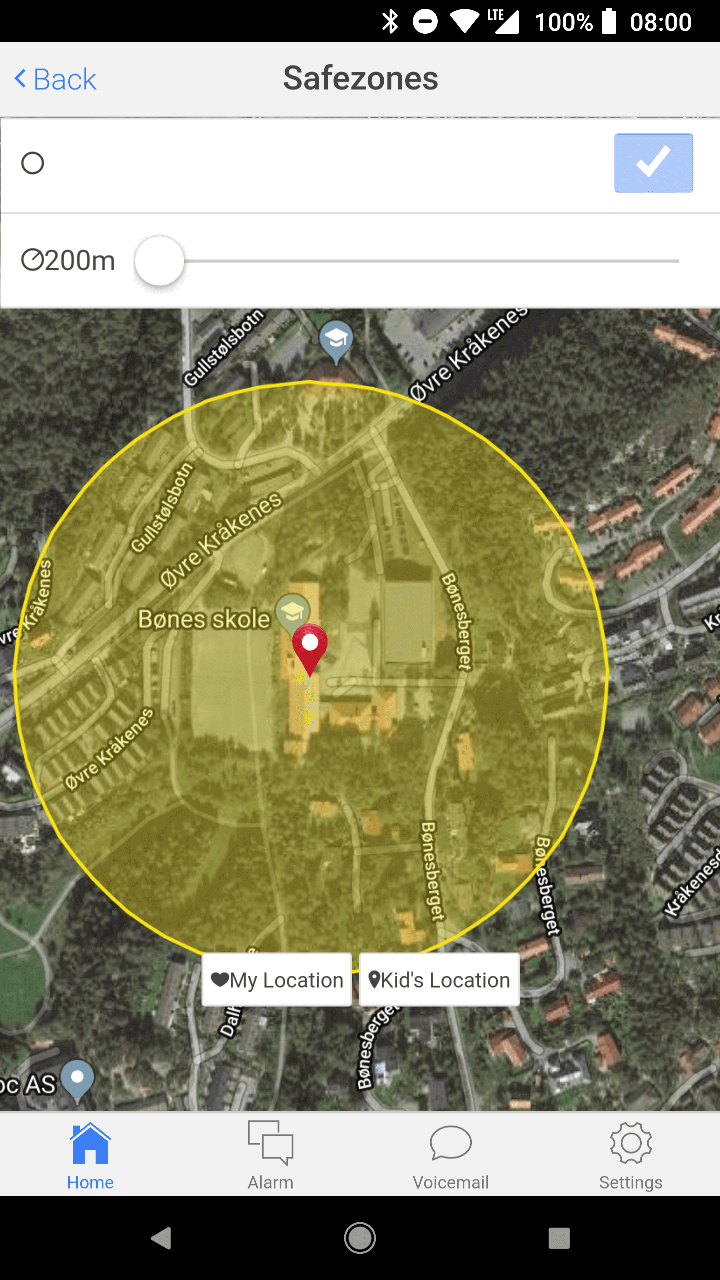
Personally it annoys me that the map where you can see the watch now doesn't have a satellite mode.
The latter two features I hope to see back in a coming version of the app.
My verdict
I will never understand how a company can buy a product like this from China and not offer data security one single thought before releasing it into the market. That being said, from what I can see, Gator Norge now has put a lot of effort to make the watch, apps and server properly secure. I'm impressed by how they have handled the criticism, pressure and technical challenges. This has not been cheap and have also cost a lot of time and effort.Judging from what Gator Norge has said they have had third party companies developing the app and doing security testing of it. As I understand it they will keep having regular audits of the products - and that is really the only serious way of handling security in such a product.
Conclusion 🔗
In Norway we are very fortunate to have watch dogs like the Norwegian Consumer Council (NCC) and Norwegian Data Protection Authority (Datatilsynet). I think they do a great job. It's so good to see them put the focus on IT security and to force through changes. It makes us all more safe and secure.
And I'm also happy to see - at least the Norwegian version of - Gator taking this seriously, being humble and saying sorry, and to return with a much more secure product. I for one, will let my kids wear this watch now.